Difference between revisions of "VPN Site-to-Site networking"
The Wiki of Unify contains information on clients and devices, communications systems and unified communications. - Unify GmbH & Co. KG is a Trademark Licensee of Siemens AG.
(→Important informations) |
|||
| (9 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
| − | + | {{Breadcrumb|0|0|Communications Systems}} | |
| − | {{ | ||
| − | |||
| − | |||
| − | |||
| − | |||
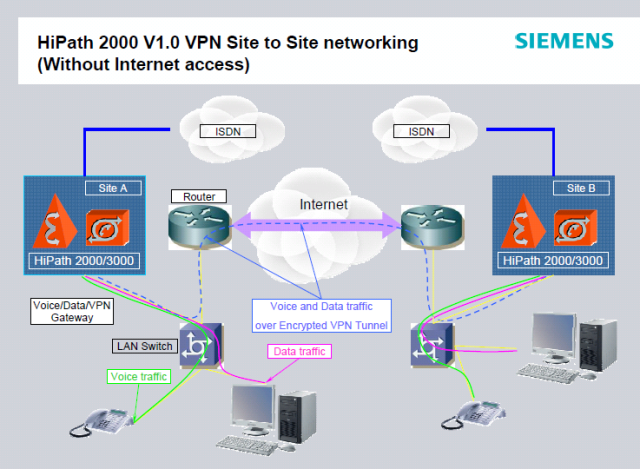
== VPN without normal Internet traffic == | == VPN without normal Internet traffic == | ||
| − | This Site-to-Site networking scenario lets | + | This Site-to-Site networking scenario lets enterprises to use: |
| − | * HiPath 2000 as [[VPN]] | + | * HiPath 2000 as Site-to-Site [[VPN]] gateway both for Voice and Data traffic. |
| − | * HiPath 2000 as a cost-effective gateway to route [[VoIP]] traffic by | + | * HiPath 2000 as a cost-effective gateway to route [[VoIP]] traffic by performing SIP and [[CorNet]]-IP IP trunking between sites over [[VPN]] trunk. |
| − | * HiPath 2000 as gateway to access enterprise resources and applications available on the company’s VPN networked sites. | + | * HiPath 2000 as gateway to access enterprise resources and applications available on the company’s [[VPN]] networked sites. |
=== Overview === | === Overview === | ||
| − | VPN Site-to-Site networking | + | [[Image:H2k_VPN_StS_Networking_1.png|HiPath 2000 VPN Site-to-Site networking scenario without normal Internet traffic]] |
=== Important informations === | === Important informations === | ||
* Basic bandwidth reservation for Voice can be implemented on HiPath 2000 setting: | * Basic bandwidth reservation for Voice can be implemented on HiPath 2000 setting: | ||
| − | ** Outgoing Bandwidth Control | + | ** Outgoing Bandwidth Control. |
| − | ** B-Channels limitation | + | ** B-Channels limitation. |
| − | * No external Firewall is required at site (HiPath 2000 features firewalling service) | + | * No external Firewall is required at site (HiPath 2000 features firewalling service). |
* If, at some point, ''normal'' Internet traffic (like Web navigation, Mail server access, etc.) is required by the Customer, then Hipath 2000 VPN Site-to-Site networking implementation must be designed according to [[#VPN with normal Internet traffic|VPN with normal Internet traffic]] scenario. In that case: | * If, at some point, ''normal'' Internet traffic (like Web navigation, Mail server access, etc.) is required by the Customer, then Hipath 2000 VPN Site-to-Site networking implementation must be designed according to [[#VPN with normal Internet traffic|VPN with normal Internet traffic]] scenario. In that case: | ||
| − | ** Customer need to ensure itself with additional ISP connection to Internet | + | ** Customer need to ensure itself with additional ISP connection to Internet. |
** Customer need to ensure additional devices/services like: | ** Customer need to ensure additional devices/services like: | ||
| − | *** Router, necessary to route LAN hosts normal | + | *** Router, necessary to route LAN hosts normal traffic to Internet. |
| − | *** Firewall, necessary to protect LAN hosts and implement [[DMZ]] at site | + | *** Firewall, necessary to protect LAN hosts and implement [[DMZ]] at site. |
| − | *** Proxy, necessary to implement Internet traffic policies | + | *** Proxy, necessary to implement Internet traffic policies. |
== VPN with normal Internet traffic == | == VPN with normal Internet traffic == | ||
| Line 40: | Line 35: | ||
* Normal Internet traffic completely separated from Voice traffic by means of second Internet connection to ISP: | * Normal Internet traffic completely separated from Voice traffic by means of second Internet connection to ISP: | ||
| − | ** Voice quality over VPN is preserved from normal Internet traffic side effects (No Voice/Date traffic congestion, no burstly data traffic or high downstream can jam Voice connections) | + | ** Voice quality over [[VPN]] is preserved from normal Internet traffic side effects (No Voice/Date traffic congestion, no burstly data traffic or high downstream can jam Voice connections). |
| − | ** HiPath 2000 can manage VPN Bandwidth entirely (No Bandwith share with normal Internet traffic) | + | ** HiPath 2000 can manage [[VPN]] Bandwidth entirely (No Bandwith share with normal Internet traffic). |
| − | ** HiPath 2000 lightweight processing power requirements handling and routing only Voice traffic over VPN Trunk. | + | ** HiPath 2000 lightweight processing power requirements handling and routing only Voice traffic over [[VPN]] Trunk. |
| − | * Routing/Security policies demanded | + | * Routing/Security policies demanded to external Proxy/Firewall devices for normal unencrypted Internet traffic handling. |
== VPN with normal Internet traffic and QoS support == | == VPN with normal Internet traffic and QoS support == | ||
| Line 53: | Line 48: | ||
=== Important informations === | === Important informations === | ||
| − | VPN Site-to-Site | + | * The [[ISP]] must support [[QoS]] to ensure sufficient voice packet quality (According to specific [[SLA]]) |
| − | + | * HiPath 2000 as [[VPN]] Site-to-Site gateway to a single ISP access, used for both: | |
| − | * HiPath 2000 | + | ** Voice and Data traffic. |
| − | + | ** Normal Internet traffic. | |
| − | + | * HiPath 2000 as a cost-effective gateway to route: | |
| − | + | ** [[VoIP]] traffic by performing [[CorNet]]-IP trunking between sites over VPN trunk. | |
| − | + | ** normal Internet traffic to ISP. | |
| − | Proxy must be | + | ** traffic to [[DMZ]] at site. |
| − | + | * External additional Proxy/Firewall: | |
| − | + | ** must be capable to handle traffic carried by [[VPN]] transparently. | |
| − | + | ** offer high level of Security for normal unencrypted Internet traffic | |
| − | + | * HiPath 2000 as gateway to access enterprise resources and applications available on the company’s [[VPN]] networked sites. | |
| − | + | * The ISP access can be overloaded (Available bandwidth could be used by massive or bursty downloads) affecting Voice quality first (Bursty data traffic, high downstream can jam Voice connections). | |
| − | + | * Operation of public servers on ([[DMZ]]) is only recommended QoS can be provided by [[ISP]] and access Router is able to support bandwidth control for both Voice and Data traffic. | |
| − | + | * Not all ISPs are able nor have a suitable infrastructure ready to offer adequate/any [[QoS]] features on their Internet access. | |
| − | |||
| − | |||
| − | The | ||
| − | Operation of public servers | ||
| − | |||
Latest revision as of 10:54, 24 April 2011
Contents
VPN without normal Internet traffic
This Site-to-Site networking scenario lets enterprises to use:
- HiPath 2000 as Site-to-Site VPN gateway both for Voice and Data traffic.
- HiPath 2000 as a cost-effective gateway to route VoIP traffic by performing SIP and CorNet-IP IP trunking between sites over VPN trunk.
- HiPath 2000 as gateway to access enterprise resources and applications available on the company’s VPN networked sites.
Overview
Important informations
- Basic bandwidth reservation for Voice can be implemented on HiPath 2000 setting:
- Outgoing Bandwidth Control.
- B-Channels limitation.
- No external Firewall is required at site (HiPath 2000 features firewalling service).
- If, at some point, normal Internet traffic (like Web navigation, Mail server access, etc.) is required by the Customer, then Hipath 2000 VPN Site-to-Site networking implementation must be designed according to VPN with normal Internet traffic scenario. In that case:
- Customer need to ensure itself with additional ISP connection to Internet.
- Customer need to ensure additional devices/services like:
- Router, necessary to route LAN hosts normal traffic to Internet.
- Firewall, necessary to protect LAN hosts and implement DMZ at site.
- Proxy, necessary to implement Internet traffic policies.
VPN with normal Internet traffic
Overview
VPN Site-to-Site networking with normal Internet traffic Overview here
Important informations
- Normal Internet traffic completely separated from Voice traffic by means of second Internet connection to ISP:
- Voice quality over VPN is preserved from normal Internet traffic side effects (No Voice/Date traffic congestion, no burstly data traffic or high downstream can jam Voice connections).
- HiPath 2000 can manage VPN Bandwidth entirely (No Bandwith share with normal Internet traffic).
- HiPath 2000 lightweight processing power requirements handling and routing only Voice traffic over VPN Trunk.
- Routing/Security policies demanded to external Proxy/Firewall devices for normal unencrypted Internet traffic handling.
VPN with normal Internet traffic and QoS support
Overview
VPN Site-to-Site networking with normal Internet traffic and QoS support Overview here
Important informations
- The ISP must support QoS to ensure sufficient voice packet quality (According to specific SLA)
- HiPath 2000 as VPN Site-to-Site gateway to a single ISP access, used for both:
- Voice and Data traffic.
- Normal Internet traffic.
- HiPath 2000 as a cost-effective gateway to route:
- External additional Proxy/Firewall:
- must be capable to handle traffic carried by VPN transparently.
- offer high level of Security for normal unencrypted Internet traffic
- HiPath 2000 as gateway to access enterprise resources and applications available on the company’s VPN networked sites.
- The ISP access can be overloaded (Available bandwidth could be used by massive or bursty downloads) affecting Voice quality first (Bursty data traffic, high downstream can jam Voice connections).
- Operation of public servers on (DMZ) is only recommended QoS can be provided by ISP and access Router is able to support bandwidth control for both Voice and Data traffic.
- Not all ISPs are able nor have a suitable infrastructure ready to offer adequate/any QoS features on their Internet access.